Earlier this month, a new strain of the Ransomware malware that goes by the name “Tyrant Ransomware” was discovered by G Data security researcher Karsten Hahn. Part of the DUMB ransomware family, Tyrant has spread across Iran through versions of Psiphon VPN to extort infected users of the popular VPN app.
Iran CERTCC (Iran Computer Emergency Response Team Coordination Center) released a security alert about Tyrant ransomware that has been widely distributed across the country.
“Attackers use whatever bait may lead users to install their malware, and are known to customize their attacks to make them more effective against specific groups or niches. So, it’s not surprising that users looking for security and privacy software are targeted; several years ago we observed similar attacks (on a much larger scale than this specific incident) in the form of malware pretending to be anti-virus tools. As always, users should be careful to obtain software they install from legitimate sources. This is especially critical when installing security software, which often runs with high privileges and has access to all data on a system,” said Marco Cova, Senior Security Researcher at Lastline.
How It Works
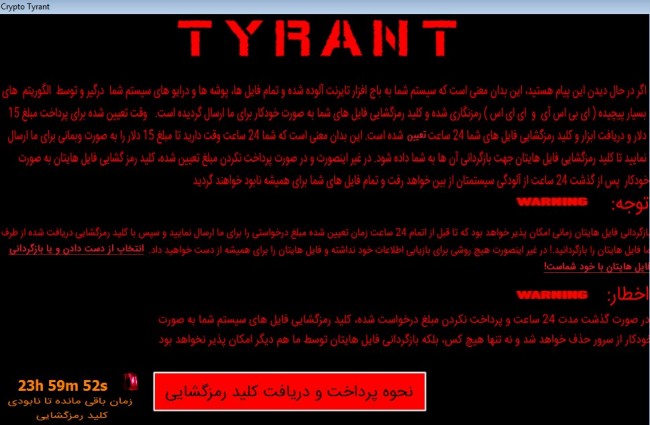
Tyrant Ransomware is created to target Iran in particular. The ransom note is released in Farsi only and it demands the victim to pay $15 within 24 hours through exchanging.ir and webmoney724.ir. Two contact email addresses are also given; Telegram username @Ttyperns and rastakhiz@protonmail.com to communicate with the infected users.
Tyrant Is DUMB
According to MalwareHunter, a security expert, Tyrant ransomware is decryptable as it is a DUMB-based malware. “A joke ransomware, without any protection (I mean obfuscation, pack, etc) used in live attack? Made my day,” MalwareHunter jokingly said to Bleeping Computer today.
This has also been confirmed by the Iran CERTCC. In a statement the Iran CERTCC said that the “Initial analysis suggests that this is the first version, or trial, of a larger attack because despite the encryption operation, sometimes the [ransomware] does not succeed in encrypting victim files, and moreover, despite the fact that there are many changes in the victim’s system registry, it is not able to maintain its functionality after rebooting the system”.
The Iran CERTCC also warned about the excess use of RDP connections especially those with weak credentials to download ransomware.


