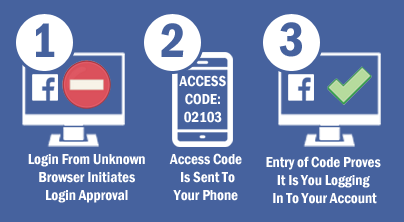
The Two Factor Authentication is one of the best things you can do to verify your records don’t get hacked. The Two Factor Authentication is a more secure strategy for checking or approving your personality.
To better secure your computerized life, turn on The Two Factor Authentication for your accounts. With a couple of minutes of set-up time, your record will be considerably more secure – with next to no bother.
The Two Factor Authentication, otherwise called 2FA, two stage check or TFA (as an acronym), is an additional layer of security that is known as “multi variable validation” that requires a secret word and username as well as something that just, and just, that client has on them, i.e. a bit of data just they ought to know or have promptly to hand -, for example, a physical token.
Validation is a critical part of PC security. All together for your PC, or an application, or a site to figure out if or not you are approved access it should first have the capacity to figure out who you are.
The Two Factor Authentication is a basic element that requests more than simply your secret key. It obliges both “something you know” (like a watchword) and “something you have” (like your telephone). After you enter your secret word, you’ll get a second code sent to your telephone, and when you enter it will you get into your record. Consider it entering a PIN number, and then getting a retina sweep, similar to you find in every spy motion picture ever constructed. It’s a great deal more secure than a secret word (which is exceptionally hack able), and keeps undesirable snoopers out of your on line records.
So “What you know, you have and who you are” are three essential approaches to set up your character with validation. The most widely recognized strategy for verification is the username and secret key. This may appear like two elements, yet both the username and the secret word are ‘what you know’ segments and the username is by and large open learning or effortlessly speculated. Thus, the watchword is the main thing remaining between assailants and mimicking you.
The Two Factor Authentication obliges utilizing two unique strategies, or variables, to give an extra layer of insurance. Regularly, two-variable confirmation includes utilizing either ‘what you have’ or ‘who you are’ notwithstanding the standard username and secret key
“What you have”
This system normally depends on a smart card, USB thumb drive, or some other kind of article which the client must have so as to validate. Smart cards and USB drives must be physically embedded into the PC so as to verify. There are likewise encryption tokens which show arbitrarily changing pin codes that the client must enter with a specific end goal to validate. In either occasion, an assailant would need to know your watchword (‘what you know’), furthermore be in physical ownership of your token or smart card (‘what you have’) to confirm as you.
“Who you are” is hard to imitate. A simple type of ‘who you are’ validation is a picture ID. Giving an official ID which can be checked similar to yours by goodness of your photograph being on it meets both ‘what you have’ and ‘who you are’ criteria. In any case, a personal ID isn’t extremely useful when managing PC access. Biometrics are a typical type of ‘who you are’ validation.
Numerous qualities are extraordinary to every individual, for example, fingerprints, retina examples, penmanship style, voice design, and so on. An aggressor may have the capacity to figure or split your secret key, however mimicking your unique finger impression or retina example is for all intents and purposes outlandish.
By obliging a ‘what you have’ or ‘who you are’ consider expansion to the standard username and secret key, two-variable confirmation gives considerably better security and makes it a great deal more troublesome for an aggressor to imitate you and access your PC, accounts, or different assets.
Tragically, you can’t utilize two-component confirmation all over on the web just yet. However, great deals of destinations have as of late executed it, including a significant number of our most loved administrations.