if you’re always on the move or rely mostly on your hand device (e.g: smartphone or tablet) to surf the web, you definitely need to secure your internet even if you’re using a home network because an insecure hand device is a an easy target for hackers or phishers to spread malware or steal your personal data (like: credit card information or passwords). If you’re looking for a way to browse the web safely without spending much on security services or creating a mess while setting up a VPN, for instance; an SSH tunnel is your saviour. SSH is a versatile and a user-friendly tool to secure your internet traffic on all operating systems, like: Windows, Mac, Linux and Android. In this article we will explain how you can secure Android with SSH tunnelling in a breeze.
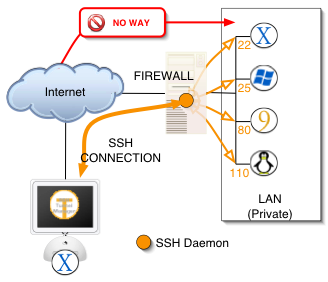
What is SSH Tunnel?
In a Nutshell…
How to Secure Android with SSH Tunnelling?
Assuming that you have already installed and set up an SSH server, like: OpenSSH, and that you have also you properly forwarded the port your SSH server is running on. Therefore, your SSH server is now accessible from the Internet.
Here is a step-by-step tutorial on how to secure Android with SSH tunnelling easily, without any hassle.
1- In order to properly secure Android with SSH tunnelling, you need to first install a free app called “Connectbot”.
2- After installing Connectbot, open it and insert the IP address (or dynamic domain name) followed by the port on which the SSH server is running and connect.
3- Once you’re connected, tap on the “Menu” button and choose “Port Forwards”.
4- In this step, you can easily configure in order to to be used for tunnelling. Tap on the Menu button and select “Add ports”.
5- A dialog box will be pop up in which you can configure 2 types of ports:
• The first port you can configure for a secure Android SSH tunnelling is mainly used for services that are already running on your home network and you want to access them through your Android device. For example, if you have a firefly media server running on a port “12345” and you want to access it from your Android device just as normally as you do over your home wi-fi, in this case you should choose “Local” as your port type. Next, insert “56000” for a source port and “ip:port” in the destination field, where the “IP” is your home local area IP and the “port” is the actual port on which server is running. Once done, open the app on your phone that wants to connects to this servier and enter “127.0.0.1” in the IP field and “56000” in the port field. That’s it!
• The second type for a secure Android SSH tunnelling on your device is used “to route all traffic to internet through home connection”. This can be done by selecting “Dynamic” and “56000” as a source port. This method doesn’t require choosing a destination port “because any traffic that comes over this tunnel will be routed back to the internet using the destination IP and port as desired, e.g., specified in a browser’s address bar.”
Furthernote
SSH tunnelling isn’t only used for maintaining online privacy. ” When you use an SSH tunnel to send data, it appears to have come from the server on the other end of the tunnel. So, somebody in Europe can use a service like Pandora by tunneling through to a server in America. Flip it the other way, and an American could use a service like Spotify by tunneling to Europe.”